Problem with mail native apps with Modern Auth & Exchange ActiveSync Disabled [Azure AD MFA]
Since iOS 11.3.1, the native mail app can support Modern Authentication. Modern Authentication is a prerequisite to apply MFA on the user.
So, if you use Modern Authentication, and that you require MFA for your users when they sign in to a O365 service, and that you have disabled ActiveSync – because it is a legacy protocol – you will have some trouble to have access to your mails.
In my case, when I onboarded a user for MFA, I disabled legacy protocols such as IMAP, POP and EAS on his mailbox, because these protocols are not secured and permit to bypass the MFA.
So, when you try to connect your O365 accounts via iOS Mail, you will obtain an error message.
The sign-in process is “Exchange” -> “Sign in using Microsoft” -> MFA prompt -> Apple Internet Accounts prompt -> “Exchange Account – Unable to verify information“.
Note : the problem is similar with other mails apps such as the Samsung mail app
In Azure AD -> Enterprise Applications -> Apple Internet Accounts, everything looks good :
- No user assignment required
- The app is granted for admin consent
If you look on the sign-in logs for the users that tried to connect their email to their iPhone, you can see (in most cases) three instances of logs; an “Interrupted”, a “Failure”, then a “Success”, all within four seconds.
The descriptions of these logs are:
- Status: Interrupted
Sign-in error code: 50058
Failure reason: Session information is not sufficient for single-sign-on. - Status: Failure
Sign-in error code: 50199
Failure reason: For security reasons, user confirmation is required for this request. Please repeat the request allowing user interaction. - Status: Success
Solution, the easy way
The Apple native app should use Legacy (Basic) authentication, even if the app supports Modern Auth.
- Using Exchange ActiveSync would push the native mobile application to a web-based authentication, which is Modern Authentication in this case.
- This would imply that EAS must always be enabled in order to perform MFA on the native mail app
You can disable IMAP and POP for your users as security recommendation but not ActiveSync if you want this to work.
So, the solution is to re-enable the EAS protocol in order to access your mails on the mail native app.
But what about the security ? How to reduce the surface attack ? How to limit the legacy protocol ?
When MSFT will disable Basic Auth in H2 2021, the native iOS app will no longer work?
Microsoft had announced that they were working on OAuth support for POP, IMAP, SMTP AUTH and Remote PowerShell protocols. Indeed, these protocols are legacy protocols that do not support OAuth by design.
However, it should be noted that EAS has never been mentioned.
After investigation, the Apple modern client should use EAS but in OAuth mode, and would not use legacy as such.
Investigation
Network trace
I take a network trace, and we can see that the native mail app uses EAS in OAuth mode :
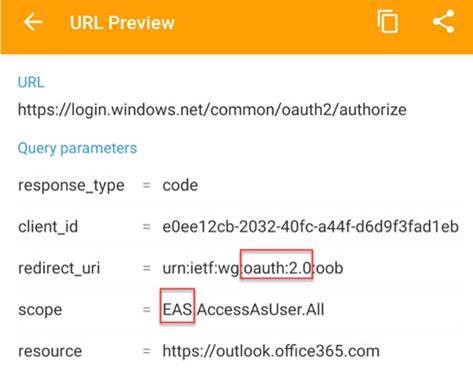
This confirms that we do not do legacy authentication in this case. But we would leave a security issue to Basic if we leave EAS activated.
Authentication Policy at the tenant level
To avoid using Basic Auth, I disables the EAS no longer at the user mailbox level but at the tenant level.
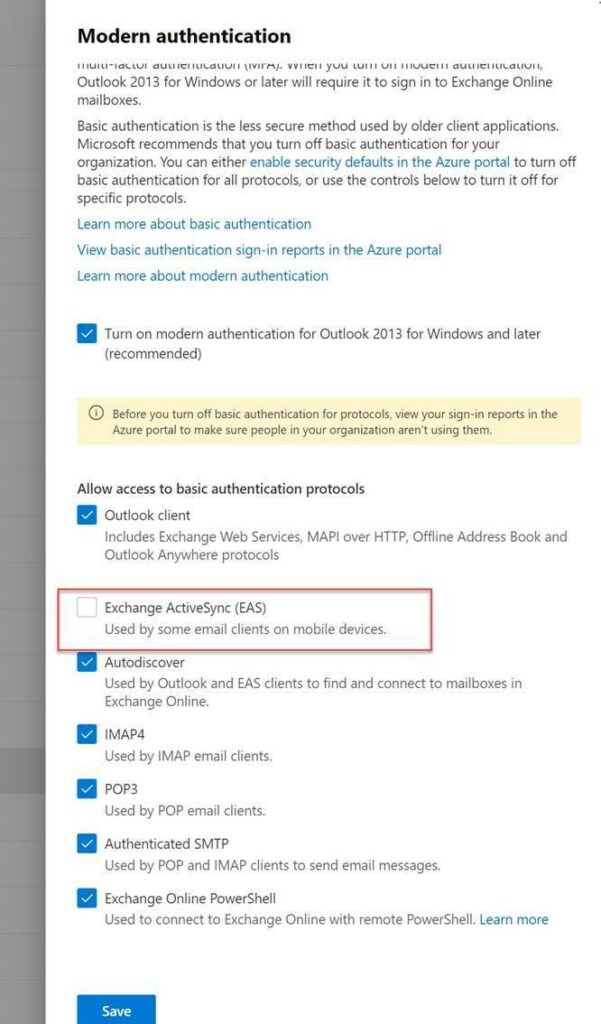
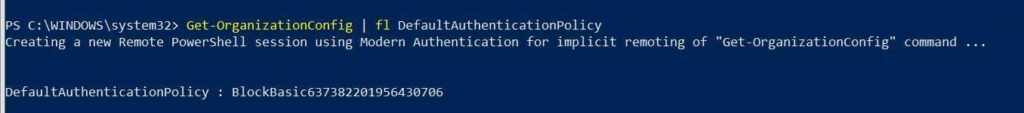
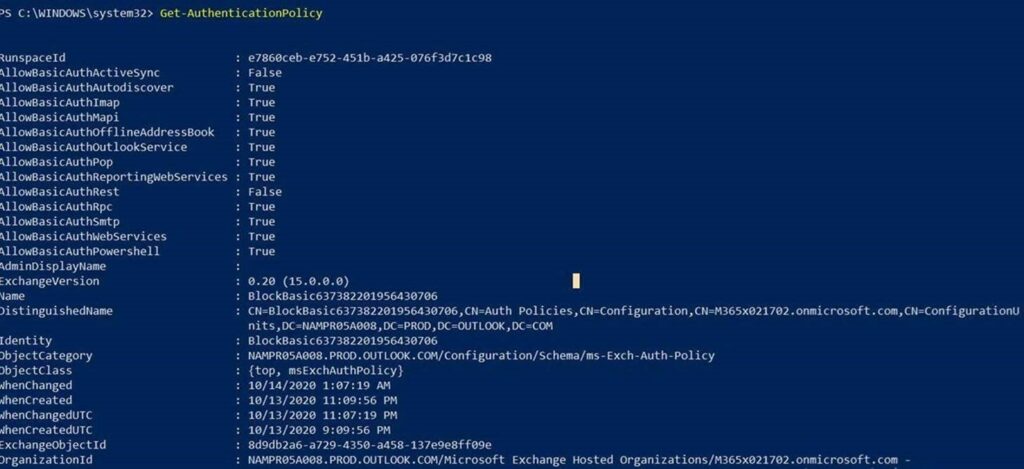
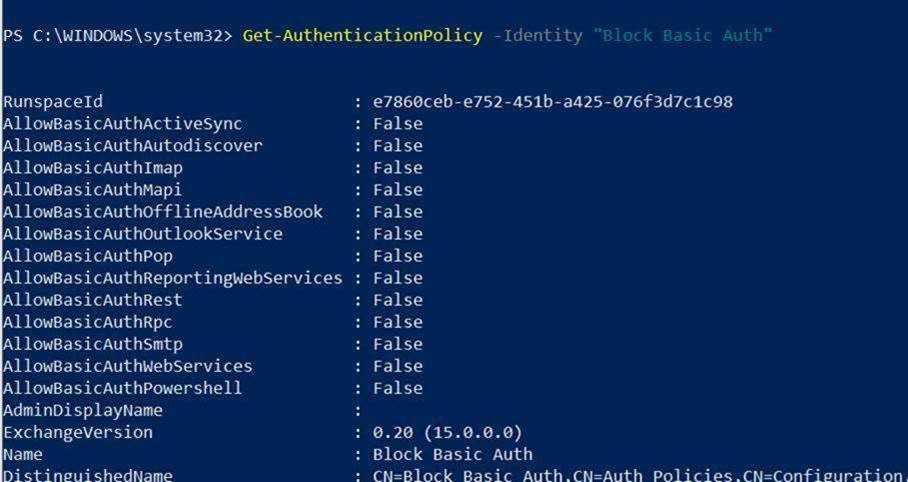
This creates an Authentication policy at the global tenant level with the AllowBasicAuthActivesync parameter in False :
Results
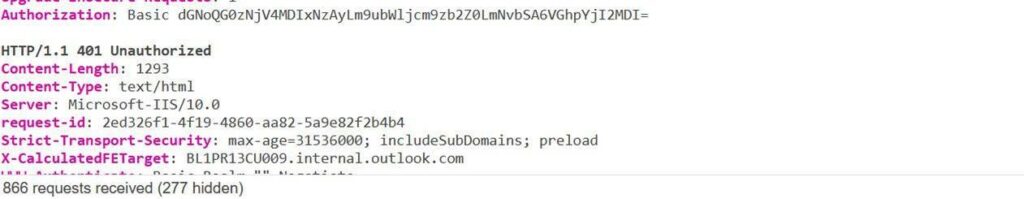
- I have access to my native mail app
- I cannot use the Basic Auth of EAS :
The solution
Be careful if you blocked the Basic Auth at the tenant level if you have some accounts that need to use it (such as service accounts).
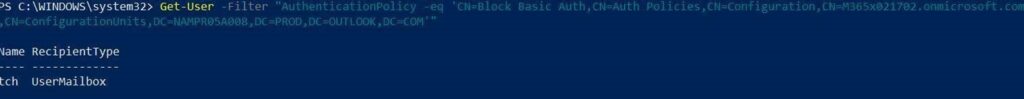
So, let the Basic Auth enabled on the tenant level and create an Authentication Policy that you can assign to your users.
To summarize :
- Create an Authentication policy
- Onboard your users to MFA and assign them the Authentication Policy

No Comments