Microsoft Endpoint Data Loss Prevention [Public Preview]
In order to accelerate the deployment of a comprehensive information protection strategy, Microsoft announcedb the public preview of Microsoft Endpoint Data Loss Prevention (DLP).
Microsoft Information Protection (MIP) is a solution that understands and classifies data, keeps it protected, and prevents data loss across M365 apps, M365 services, third-party SaaS applications…
Endpoint DLP now extends MIP classification and protection to devices.
Prerequisites
Licences
- Microsoft 365 E5/A5
- Microsoft 365 E5/A5 Compliance
- Microsoft 365 E5/A5 Information Protection and Governance.
Software
- Get the latest version of Edge Chromium that’s integrated with Endpoint DLP, on the Microsoft Edge page.
Hardware
- Windows 10, version 1607 or later
Creation of DLP policies
You only need to create DLP policies once in the Microsoft 365 compliance center.
They can then apply the policies to Exchange, Teams, SharePoint, OneDrive for Business, and now – to endpoints as well.
All that is required is for the endpoint to be onboarded in your environment using your established device management onboarding process.
Endpoint DLP identifies and protects information on endpoints. Endpoint DLP does not restrict or limit the use of applications, web browsers, or other services when sensitive data is not present.
It delivers three core capabilities:
- Native protection
- seamless deployment
- integrated insights.
Native protection
Users are automatically alerted when they take an inappropriate or risky action with sensitive data and are provided with actionable policy tips and guidance to remediate properly.
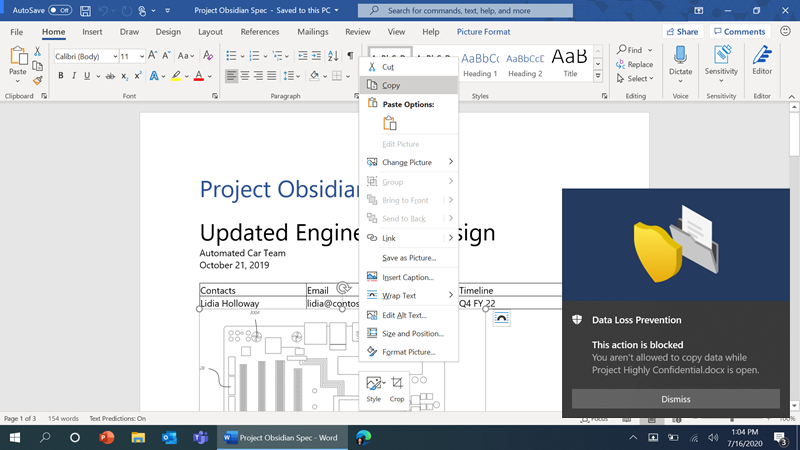
For example, a user attempts to copy sensitive data from the Word document which contains sensitive information. In this example, the policy is set as ‘Block’ without the option to Override. When the user performs the activity – in this case, copying sensitive data, the event is recorded, and the user is notified that this action is being blocked because copying this data is not allowed, per the DLP policy.
The user experience for third-party applications is similar.
For example, a user tries to copy a document with sensitive data to a personal Dropbox account using Microsoft Edge. In this example, the DLP policy is set as ‘Block with Override.’ The user is notified this action is blocked because copying the file to that specific cloud application is not allowed, and the event is recorded and available for review and analysis in the Microsoft 365 compliance center console.
Seamless deployment
Endpoint DLP is managed via the Microsoft 365 compliance center.
You can start with the 100+ built-in sensitive data types and over 40 templates for common industry regulations.
The good stuff – Audit mode for no impact on users
Microsoft DLP solutions offer three different modes to monitor and restrict activities in each DLP policy to ensure the intended compliance objectives are achieved:
- Audit: only records policy violation events without impacting end user activity
- Block with Override: records and blocks the activity, but allows the user to override when they have a legitimate business need
- Block: records and blocks the activity without the ability to override
Endpoint DLP can enforce policies for a broad range of activities unique to the endpoint including:
- Copying a sensitive file to an external USB media device
- Copying a sensitive file to a network share
- Uploading a sensitive file to a cloud service
- Printing a sensitive file
- Copying sensitive content to the clipboard
- Accessing a sensitive file by an unallowed app
Report
The Activity Explorer permits to identify risky activities and the view provides details on specific actions, user, and file details. Thus, you will be able to remediate potential risks of unintended or intentional data breaches.
Integrated insights
Microsoft Endpoint DLP integrates with other Security and Compliance solutions such as MIP, Microsoft Threat Protection, and Insider Risk Management in Microsoft 365. Endpoint DLP enriches the other solutions with precise insights about device activity of sensitive content.
Sources
To learn more about Endpoint DLP, visit documentation.







No Comments