Mitigate risks with application block in Microsoft Defender Vulnerability Management [Public Preview]
Remediating vulnerabilities in organizations takes time so it’s essential to have effective risk management strategies in place. We know that addressing software vulnerabilities can be challenging due to a variety of factors. To help with risk mitigation, Microsoft Defender Vulnerability Management (MDVM) users can leverage the application block feature to take immediate action to block all currently known vulnerable versions of applications. A feature unique to Defender Vulnerability Management, you can block vulnerable app versions for designated device groups, provide users with custom warning messages, and provide links to your organization’s internal sites where you can provide more information on the policy. This premium capability is available to Defender Vulnerability Management add-on and standalone users.
With the application block feature, you can do the following:
- Take action to block / warn against the use of vulnerable applications
- Review applications versions blocked by this mitigation
- Review file hash indicators created by this mitigation
- Notify end users when an application is blocked on their device
- Review detections related to this policy via Advanced Hunting
You can access this feature in Microsoft 365 Defender portal. After ensuring all your onboarded devices meet the minimum requirements, head over to the vulnerability management section in the left-hand navigation pane where you will find security recommendations related to software installed in your organization.
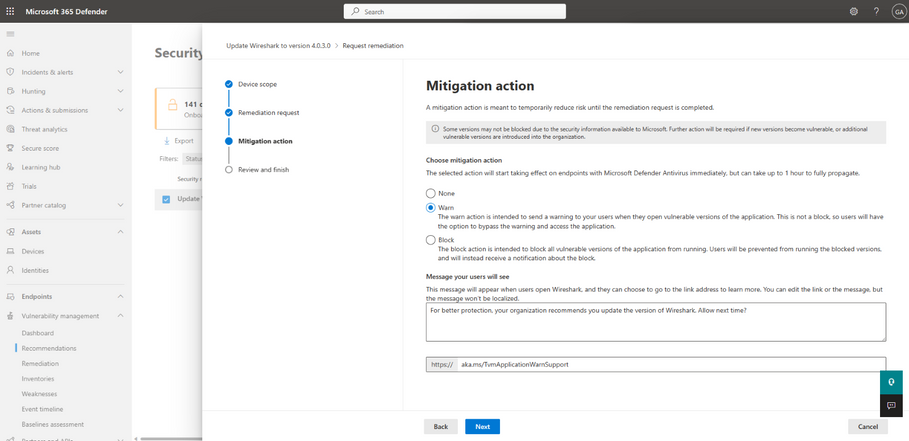
Review security recommendations and mitigate vulnerabilities
Security recommendations for some Windows software will offer two mitigation options:
- Block policies ensure that relevant files associated with this application are not allowed to run.
- Warn policies provide the end user with the ability to bypass the block.
For both actions, you can customize the message the users will see. For example, you can encourage them to install the latest version. Additionally, you can provide a custom URL the users will navigate to when they select the notification.
Manage blocked applications
When a mitigation action has been created, allow up to 30 minutes for that policy to be applied to your devices. To review the application versions that will be blocked by your policy, head over to ‘Remediation > Blocked applications’ and select the application from the list. Here you will see the blocked versions as well as the device groups that this software is being blocked on.

Review file indicators related to this mitigation
You can also review the specific file hashes that have been blocked in association with this application by clicking ‘View details of blocked versions in the indicator page’. This will redirect you to the indicators settings page and automatically filter down to the file hashes associated with that application. Here, you can export the complete list of indicators for internal reporting and testing.

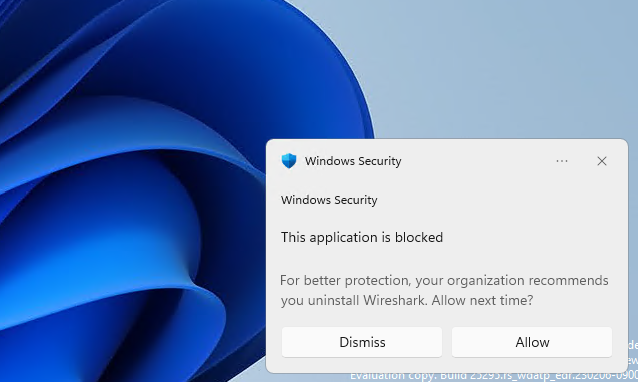
Notify end users using default or custom messaging
When attempting to launch an application blocked by your policy, your end users will see a notification that this application was blocked by their admin. Clicking the ‘allow’ button will bypass the block for subsequent launches. The user is required to relaunch the application after clicking the allow option.
Verify effectiveness of your policy
To review the effectiveness of your application block policy, you can head over to Advanced Hunting and review antivirus detections. Application block detections are surfaced in the DeviceEvents table. Using KQL, you can modify your query to search for a specific application based on the attributes such as the file hash or file name. Here is a sample query you can use for your own searches. Note that you must specify “TVMBlock” or “TVMWarn” (dependent on your policy) for the AdditionalFields to ensure you are filtering down to the application block detections.
DeviceEvents
| where ActionType == “AntivirusDetection”
| where AdditionalFields contains “TVMBlock”
| where FileName contains “example.exe”
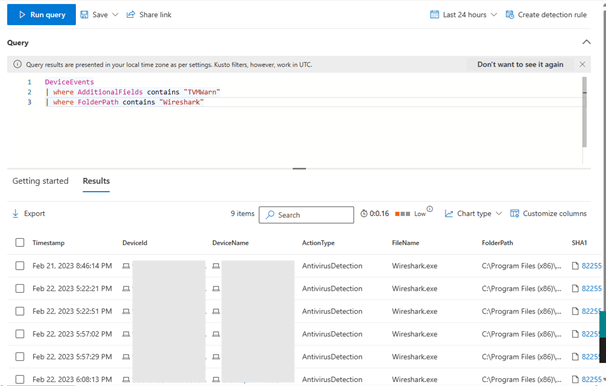
You also search for specific file paths, specific devices with this block and many other details via advanced hunting to ensure that your blocks are taking effect.
In summary, MDVM application block empowers security administrators to block known vulnerabilities in their organization so they can rest assured that their sensitive workloads are safe.
Source
Mitigate risks with application block in Microsoft Defender Vulnerability Management

No Comments