Intune – Migrating between Mobile Threat Defense solutions
Intune can integrate data from Mobile Threat Defense (MTD) solutions such as Microsoft Defender for Endpoint and other non-Microsoft MTD partners as an information source for unenrolled devices using Intune app protection policies (APP).
Admins can use this information to help protect corporate data within an Intune protected app and issue a block or selective wipe through APP conditional launch settings if the MTD determines a user’s device is in an unsecured or compromised state.
Historically, only one MTD connector (per operating system) could be active in an Intune tenant for APP usage at a time. This led to difficulty in MTD migration scenarios where APP integration would need to be fully disabled in the existing MTD connector tenant-wide prior to enabling APP integration on the connector the organization intended to migrate to.
With Intune’s 2210 (October) service release, organizations are now able to enable Defender for Endpoint in addition to one non-Microsoft MTD connector on the same tenant for APP usage to help facilitate MTD migrations.
Note: Only migrating to or from Defender for Endpoint and a non-Microsoft MTD solution is supported. Migrating between two non-Microsoft MTD solutions is not supported.
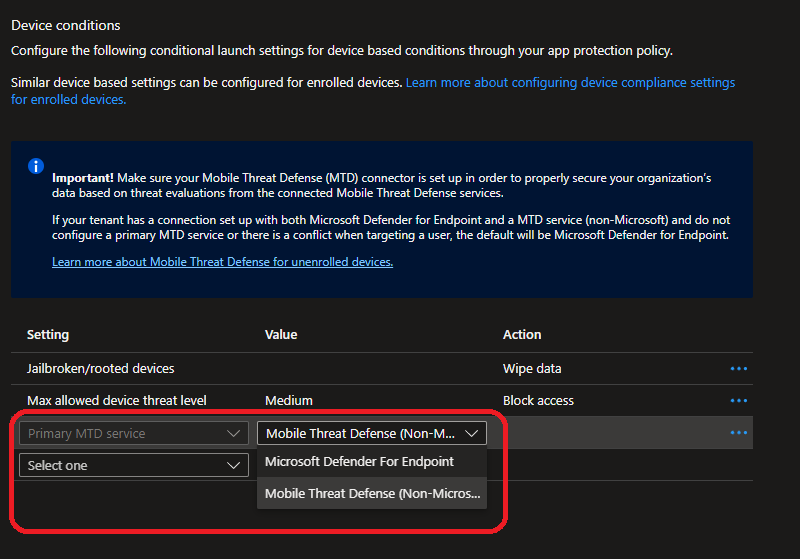
As part of this, Microsoft has introduced a new APP setting, Primary MTD service, that helps determine which threat signal source (Defender for Endpoint or non-Microsoft MTD) should be authoritative in instances when a tenant has both connectors enabled for an OS platform and a targeted user’s apps need to be evaluated through the conditional launch process.
Admins will now be able to create and assign multiple app protection policies targeting different groups of users with different primary threat signal services. This new functionality enables organizations to:
- Migrate from a non-Microsoft MTD to Defender for Endpoint in a staged rollout rather than a tenant-wide, direct cutover from one service to the other.
- Migrate from Defender for Endpoint to a non-Microsoft MTD in a staged rollout rather than a tenant-wide, direct cutover from one service to the other.
- Migrate between MTD services without needing to pause risk score detection during the transition period.
Configuration
Before enabling APP integration for a given OS in the second connector, modify your APP policies to ensure that users are assigned the proper Primary MTD service.
Note: The Primary MTD service setting has no effect if only one connector is enabled in the tenant for APP on the given OS platform. If “Max allowed device threat level” is set to any value, only the configured connector for that OS will be used, even if it does not match the connector specified in the primary value.
Then, in the Intune admin center, navigate to the Connectors and tokens pane within Tenant Administration. Enable the respective OS integration for APP functionality under Microsoft Defender for Endpoint in addition to the existing MTD under Mobile Threat Defense, where it is already enabled (or vice-versa, depending on which service your organization is migrating to).
User Experience
If a set of users have already configured and registered with a non-Microsoft MTD or MDE and are then targeted with a new primary threat signal service, there are two things that need to occur before they’re prompted to set up the new service on their device.
- The APP conditional launch Primary MTD service setting needs to be applied to the user’s app (For check-in timing estimates, see Understand App Protection policy delivery and timing.)
- Once the new policy setting is applied, the app needs to process a conditional launch evaluation. Timing here may vary based on your configuration for the APP setting, Recheck the access requirements after (minutes of inactivity).
Note: On Android, Company Portal v5.0.5662.0 or higher is required to support the MTD migration scenario. On iOS, the protected client apps must have integrated an Intune SDK version that supports MTD conditional launch evaluation (v12.0.15 or higher).
Once these two activities have occurred, the user will be blocked by conditional launch and required to configure the new threat signal service on their device. Once Intune has received the threat signal from the new service (and it’s within the allowed threshold), the user can access the Intune protected app and remove the previous MTD app from their device.
See the table below to determine the expected behavior when Primary MTD service setting is configured for each scenario.
| Primary MTD service configuration | Defender connector enabled only | Non-Microsoft MTD connector enabled only | Both connectors enabled |
| Defender (MDE) | MDE enforced | Non-Microsoft MTD enforced | MDE enforced |
| Non-Microsoft MTD | MDE enforced | Non-Microsoft MTD enforced | Non-Microsoft MTD enforced |
| Conflict (multiple policies, different primary services) | MDE enforced | Non-Microsoft MTD enforced | MDE enforced |
| None configured | MDE enforced | Non-Microsoft MTD enforced | MDE enforced |
Note: This table assumes the app protection policy also contains a conditional launch maximum allowed threat level requirement. If there is no maximum threat level requirement in the app protection policy, the Primary MTD service setting is ignored. Additionally, targeting the same user(s) with different Primary MTD configurations across multiple apps on the same OS is unsupported and may result in unpredictable behavior. (For example, Outlook on iOS requires MDE while OneDrive for iOS requires non-Microsoft MTD). Determine your required Primary MTD service setting on a per-user/OS platform basis rather than per-user/app basis.
Source
Intune app protection: Migrating between Mobile Threat Defense solutions – Microsoft Community Hub


No Comments