Azure Sentinel – Microsoft 365 Defender (MTP) connector now in Public Preview
The 09 November, Microsoft announced that the public preview of the new Microsoft 365 Defender connector is now available.
The M365 Defender connector lets you stream advanced hunting logs – a type of raw event data – from Microsoft 365 Defender into Azure Sentinel.
It will permit to give you a complete access to the full set of advanced hunting logs, and allow you to do the following:
- Easily copy your existing Microsoft Defender ATP advanced hunting queries into Azure Sentinel.
- Use the raw event logs to provide additional insights for your alerts, hunting, and investigation, and correlate events with data from additional data sources in Azure Sentinel.
- Store the logs with increased retention, beyond Microsoft Defender for Endpoint or Microsoft 365 Defender’s default retention of 30 days. You can do so by configuring the retention of your workspace or by configuring per-table retention in Log Analytics.
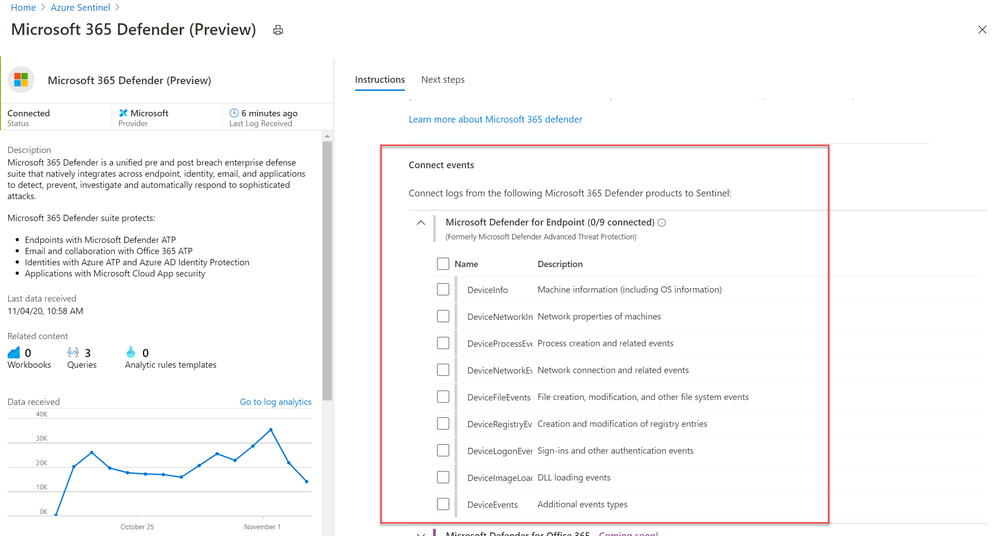
Prerequisites
- You must have a valid license for Microsoft Defender for Endpoint, as described in Set up Microsoft Defender for Endpoint deployment.
- Your user must be assigned the Global Administrator role on the tenant (in Azure Active Directory).
Integration
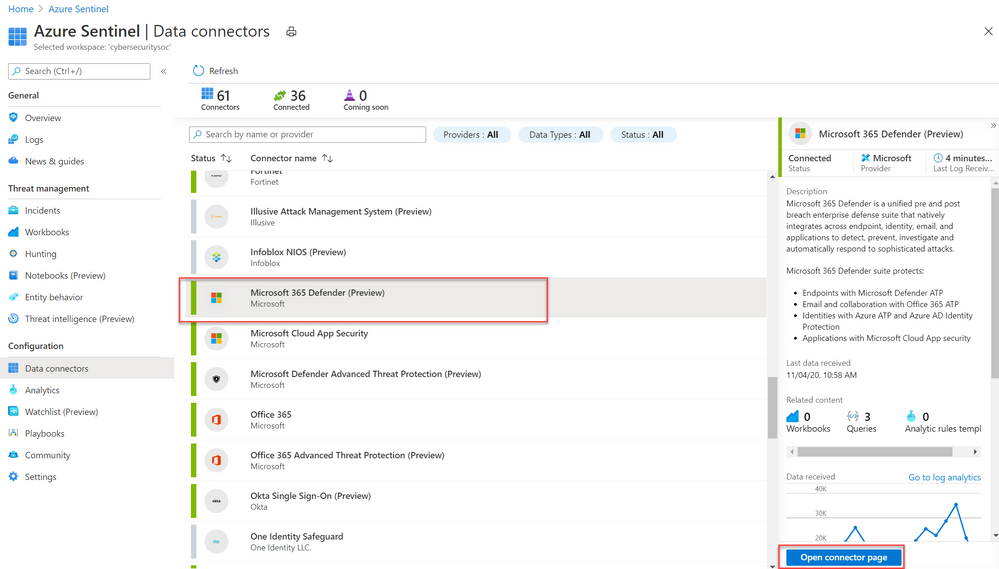
- From the Azure Sentinel navigation menu, select Data connectors.
- Select Microsoft 365 Defender from the data connectors gallery, and then select Open Connector Page on the preview pane.
- On the Microsoft 365 Defender connector page, under Connect events and Microsoft Defender for Endpoint tick the boxes for the types of logs you would like to be sent to Azure Sentinel and select Apply Changes.

No Comments