Shadow Protection – MDATP [Private Preview]
When Shadow Protection is enabled, Microsoft Defender ATP leverages behavioral blocking and containment capabilities by blocking malicious artifacts or behaviors that are observed through post-breach protection.
EDR in block mode, i.e. Shadow Protection, works behind the scenes to remediate malicious artifacts that are detected post-breach.
Prerequisites
- Permissions
Global Administrator or Security Administrator role assigned in Azure Active Directory.
See Basic permissions. - Operating system
– Windows 10
– Windows Server 2016 or later - Windows E5 enrollment
– Microsoft 365 E5
– Microsoft 365 E3 together with the Identity & Threat Protection offering
See Components and features and capabilities for each plan - Cloud-delivered protection enabled
See Enable cloud-delivered protection. - Windows Defender Antivirus antimalware client up to date
Using PowerShell, run the Get-MpComputerStatus cmdlet as an administrator.
In the AMProductVersion line, you should see 4.18.2001.10 or above. - Windows Defender Antivirus engine up to date
Using PowerShell, run the Get-MpComputerStatus cmdlet as an administrator.
In the AMEngineVersion line, you should see 1.1.16700.2 or above.
Configuration
- Go to the Microsoft Defender Security Center (https://securitycenter.windows.com)
- Go to Settings > Advanced features.
- Turn on EDR in block mode.
Result
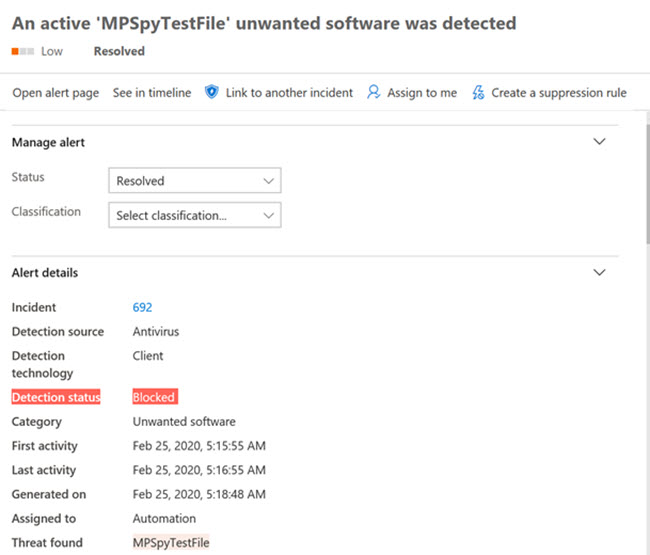
When a malicious artifact is detected, blocking and remediation actions are taken.
You will see detection status as Blocked or Remediated as completed actions in the Action center.

No Comments