O365 ATP Campaign Views and Compromised User Detection and Response – GA [EN]
Last Friday, Microsoft announced the general availability of two extremely popular and valuable features in the Office 365 Advanced Threat Protection offering:
- Campaign Views
- Advanced Compromised user detection and response.
Campaign views:
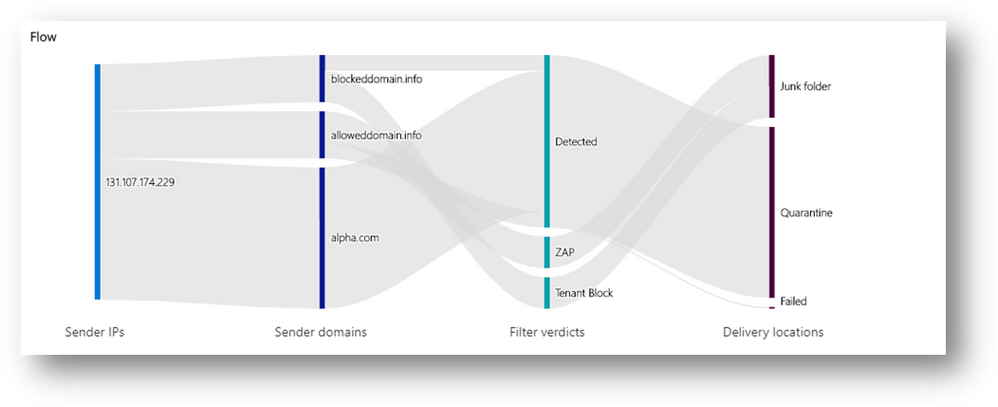
Campaign views offer security teams the full story of how attackers targeted the organization and its users and how their defenses held up (or not).
Benefits
- See summary details about the campaign, including when the campaign started, the sending pattern and timeline, how big the campaign was and how many users fell prey to it.
- See the list of IP addresses and senders used to orchestrate the attack.
- Assess which messages were blocked, ZAPped, delivered to junk or quarantine, or allowed into the inbox.
- See all the URLs that were manifested in the attack
- Learn if there are users that have fallen prey to any attacks and clicked on the phish URL.
Goals
- Remediate compromised/vulnerable users
- Improving security posture by eliminating configuration flaws seen
- Investigate related campaigns that use the same indicators of compromise
- Hunt and track threats that use the same indicators of compromise
Additional improvements:
Improved discoverability: Campaign views are a separate node in the left navigation panel of the O365 Security and Compliance portal under ‘Threat Management’.
Expanded search and investigation capabilities: Microsoft have made it easier to search across campaigns. For example, you can search for all campaigns that targeted a specific recipient or campaigns related to a particular email (search for subject keywords or the specific messageID).
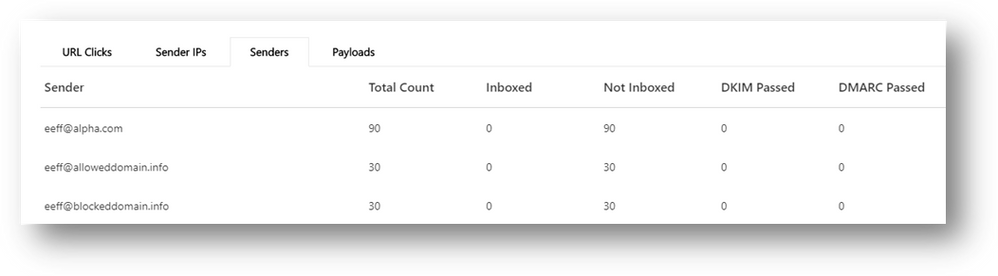
More campaign details: For each campaign, more included information is presented.
- Click-rate: As a way to measure the effectiveness of the campaign (from an attackers perspective), or in other words the impact of the campaign on the organization, Microsoft now shows off a click-rate. Click-rate shows the percentage of Inbox’ed messages (messages delivered to the Inbox) that received a click from the recipient. This is an indirect measurement how effective and convincing the social engineering aspect of the campaign was.
- Authentication details: Within the Campaign view, Microsoft shows expanded authentication details: all email authentication protocols (SPF for sending IPs, DKIM and DMARC for senders). Authentication failures identify attackers that are spoofing senders. Passing these authentication checks indicates a legitimate email sending infrastructure is being used for these attacks (for example, compromise or abusive activities that would require different action plans).
Advanced Compromised user detection and response:
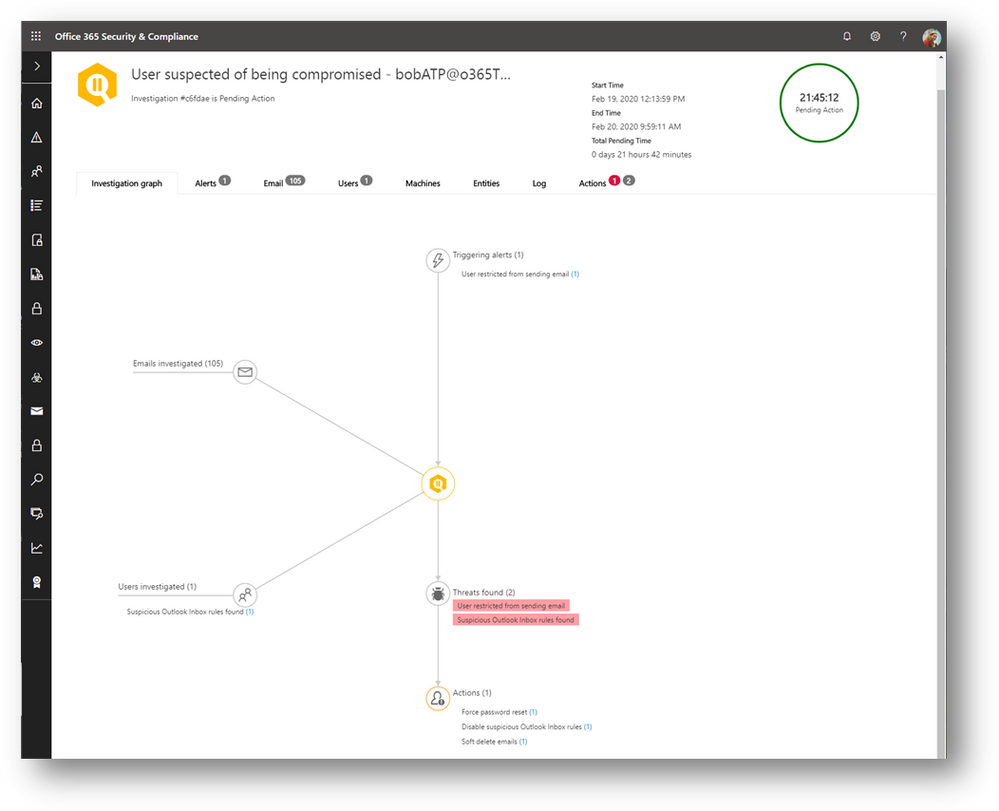
The attacker’s activities when using a compromised account are often atypical or anomalous relative to the user’s regular behavior. For instance, there is no good reason for trusted users to be sending any phish or spam emails to other recipients. Being able to detect anomalies in user activity is therefore a key signal source for detection.
A few months ago, Microsoft released several features to detect anomalies in user activity to expand on our detection of user compromise. And Microsoft also released into preview a compelling automated playbook to automatically investigate such threats to help security teams more effectively and comprehensively detect the source and impact of the compromise and take remediation actions.

No Comments