Microsoft has begun the rollout of security defaults to existing customers who haven’t yet rolled out security defaults or Azure AD Conditional Access.
Microsoft introduced security defaults in October 2019 for new tenants, ensuring that new customers would be created and maintained with basic security hygiene in place – especially MFA and modern auth requirements – regardless of license, but tenants created before October 2019 were not included in security defaults and were vulnerable unless they explicitly enabled features like Conditional Access, Identity Protection, and MFA.
What to expect?
Security defaults challenge users with MFA when necessary, based on factors such as location, device, role, and task. Due to the power admins have to make changes to your environment, they’re required to perform MFA every time they sign in.
Based on usage patterns, Microsoft will start with organizations that are a good fit for security defaults, aka customers who aren’t using Conditional Access, haven’t used security defaults before, and aren’t actively using legacy authentication clients.
Global admins of eligible tenants will be notified through email. Then, starting in late June, they’ll receive the following prompt during sign-in:
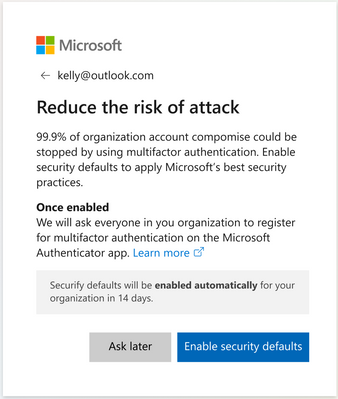
Global admins can opt into security defaults right away or snooze for as many as 14 days. They can also explicitly opt out of security defaults in this time.
After security defaults are enabled, all users in the tenant are asked to register for MFA. Again, there is a grace period of 14 days for registration. Users are asked to register using the Microsoft Authenticator app, and Global administrators are additionally asked for a phone number.

Source
Raising the Baseline Security for all Organizations in the World – Microsoft Tech Community